Are you thinking of securing your ventures vital information from dangerous criminals using Cyber Essentials? Before you select the procedure and type check out the different Information Technology requirements a Cyber Essentials demand you to provide with.
Cyber Essential is a government implemented security scheme to ensure that businesses are secured and protected from those attackers of the online world. There are specific requirements a certifying body will demand from your organization regarding the IT infrastructure to make sure that your company can provide every security need and is all set for certification.
IT Requirements:
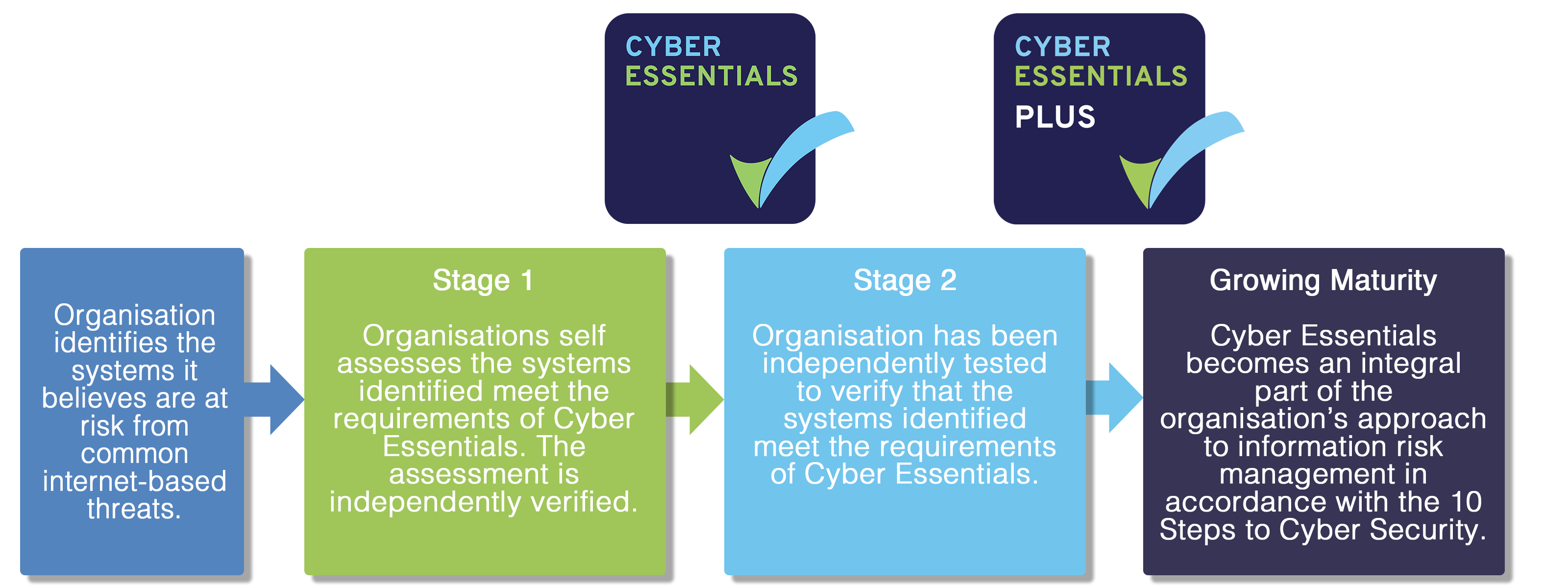
There are 2 steps towards certification requirement fulfillment.
- Set a boundary of scope
Setting a boundary means assessing the scopes where the security scheme should be laid, that is, whether the certification should cover the whole IT infrastructure or just a subset is enough. The decision should be according to unit managing the business, network restrictions and geographical location. Everything that comes under this boundary applies to the requirements to be provided and should meet the following conditions:
- Network connections from untrusted internet connected hosts should be accepted
- Outbound connections through the internet that are initiated by the user should be established
- Data flow should be controlled between the above devices and internet
- Reviewing each technical control themes and their controlling ideas as requirements.
Main 5 technical controls are:
Firewalls
Restricting your device network from getting accessed by other untrusted devices and services can reduce the threat of being exposed to attacks. Firewall rules help you to resist or block unwanted communications according to its source, destination, and type of communication protocol. To acquire certification every device in scope should be protected by a firewall or an equivalent network.
Secure Configuration
This control helps to ensure that the business computers and networks are properly configured to reduce the vulnerabilities of the connection and to make sure that only required services are provided. Certification requirement includes management of the computers and networks by removing or disabling unwanted accounts, changing guessable passwords, removing unnecessary software, etc.
User Access Control
This control makes sure that each user account is given to authorized users only and these accounts only provide access to those computer networks required for them. Applicant should have complete control over user accounts and their accessibilities, that is, they should have a process to approve while an account is created, authentication of their access before granting privileges, etc.
Malware Protection
Restriction of unwanted software and known malware from execution to prevent malware infection is the job of this control. Harmful viruses and spyware can affect the important software and unethical accessing of information from computer networks. Implementing malware protection mechanisms on all in-scope devices is the requirement needed.
Patch Management
This control is about ensuring all software and devices protected against known security issues. The software must be updated regularly, with assured vulnerability protections and remember to remove unused software as well.
To prevent cyber attackers from misusing any organization’s information, it is essential to certify with Cyber Essentials.

Share your thoughts