Did you know that more than 30,000 websites are hacked every day? And if that is not enough to scare you, in the first quarter of 2020, a survey showed that more than 70% of WordPress installations are vulnerable. Out of which, approximately 47% of the hacked WordPress websites had a backdoor. If your WordPress website was hacked recently, hackers might have left a backdoor behind. But do not worry, we have written this article to help you fix your hacked websites. Here, we will discuss the WordPress backdoor in detail with different tips and tricks to deal with it.
[tmh_article_ads]
What is a WordPress backdoor?
With an unsurprisingly massive user base, WordPress is currently the prime target of hackers. Several WordPress websites are infected, and the number is still increasing.
Backdoors in WordPress are a tricky piece of code that a hacker injects to allow remote and unauthorized access. A hacker can bypass the regular authentication procedure and gain access to the server using a backdoor.
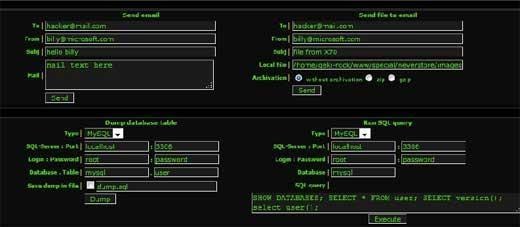
Hosting a backdoor is similar to losing the spare key of your apartment. You will not notice small changes at first, but soon all your furniture and valuables will be gone, and you will keep guessing. You can only do one thing to keep the stranger out: change the lock. In the upcoming sections, we shall discuss some steps to fix the backdoor problem. However, before that, let us see what a hidden backdoor can do to your website:
- A hacker can remotely upload/inject scripts or links to redirect your visitors to malicious links using the backdoor.
- The hacker can add him/herself as a new admin for later use.
- Manipulate your WordPress website remotely.
- Pharma or keyword hacks.
- Use the information of your clients for personal gain.
- Use your website as a host for spreading spam.
Where to look for hidden backdoors?
The sole purpose of making backdoors is to stay hidden; it is difficult to find a backdoor on a website when you do not know where to start. After thousands of cleanup, we have a slight idea as to where one can hide these backdoors.
-
Themes
If you have inactive themes lying around on your website, this might be the best time to remove them. The hacker will not hide a backdoor in your current theme, but your website’s inactive theme might work as a potential threat. The same goes for WordPress plugin files.
-
Upload directory
It is common to use WordPress’s upload directory to upload media files. But do you ever check these files? No, of course not; why would you do that. Well, now, it is a backdoor. Since this directory is writable, it is effortless for a hacker to upload vulnerable media files on your website.
-
wp-config.php
The WordPress website’s wp-config file contains all the information such as username, hostname, passwords, server name, etc. If the hacker plants a backdoor here, it will get challenging to detect. Therefore, check every line of these files; the backdoor can be either a single piece of code or a group of it.
-
wp-includes directory
The wp-includes directory contains the core files of WordPress installations. If you do not know each file by name, it might be difficult for you to detect backdoor. However, if you have a pre-hack backup of your website, restore that version. Here is a free Malware scanner that you can use to scan your site
How to remove WordPress backdoor?
-
Delete inactive themes and plugins
If you are not using a theme or plugin, why waste your space? If the backdoor were in these files, it would be gone. And even if the backdoor was not present in there, you have nothing to lose.
-
.htaccess file
You can delete the file and save your time; there is no need to go line-by-line. It is pretty challenging to find the suspicious block of a script if you are not too tech-savvy. You can recreate the .htaccess file by going to permalinks in the settings from the WordPress admin panel.
-
wp-config.php file
Compare the infected version of the wp-config file with the last clean backup of the file. If you do find discrepancies, restore the backup version.
-
Database scans
Do not forget to check newly added users. An intelligent hacker will never leave just one backdoor. The database of a WordPress website is an easy target. If you do find more users than intended, remove them.
Do you think that your website is safe now? Think again! You can never be 100% sure. Now, open your website from incognito mode; if it doesn’t show any hack, your website is safe, for now. Sometimes, the hack will not make itself known to the logged-in users; you have to look at it from the outside to get a clear idea.
Prevent future mishaps!
Cleaning your hacked website is not always enough. Sometimes, you have to strengthen your website’s security to save it from future cyber attacks. And the best way to that is by getting a security solution for your website. Astra Security Suite is the best security solution that you can get for your WordPress website at an affordable price. With more than 1000 installations, Astra is currently leading as the top WordPress security solution. You can also check out Astra’s firewall. It is equipped with handling not only backdoor hacks but also other known CVEs. The 24*7 customer support of Astra will keep you informed of all the irregularities. For more information, visit Astra’s official website.



Share your thoughts